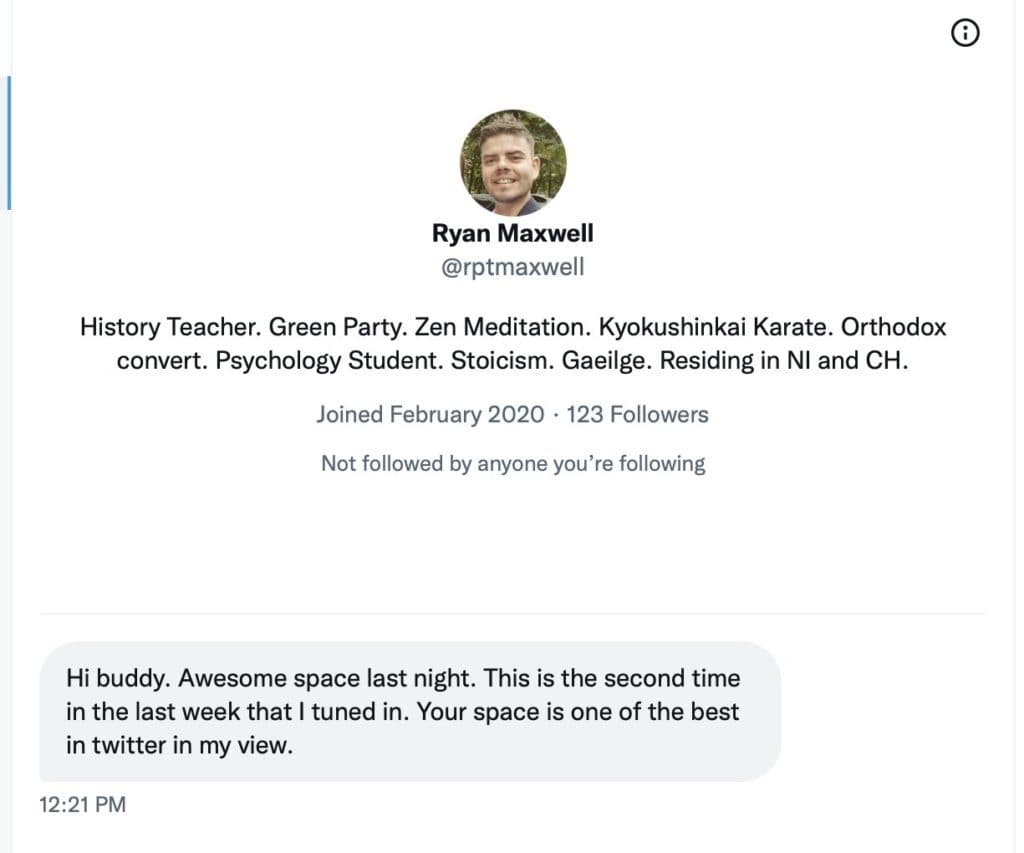
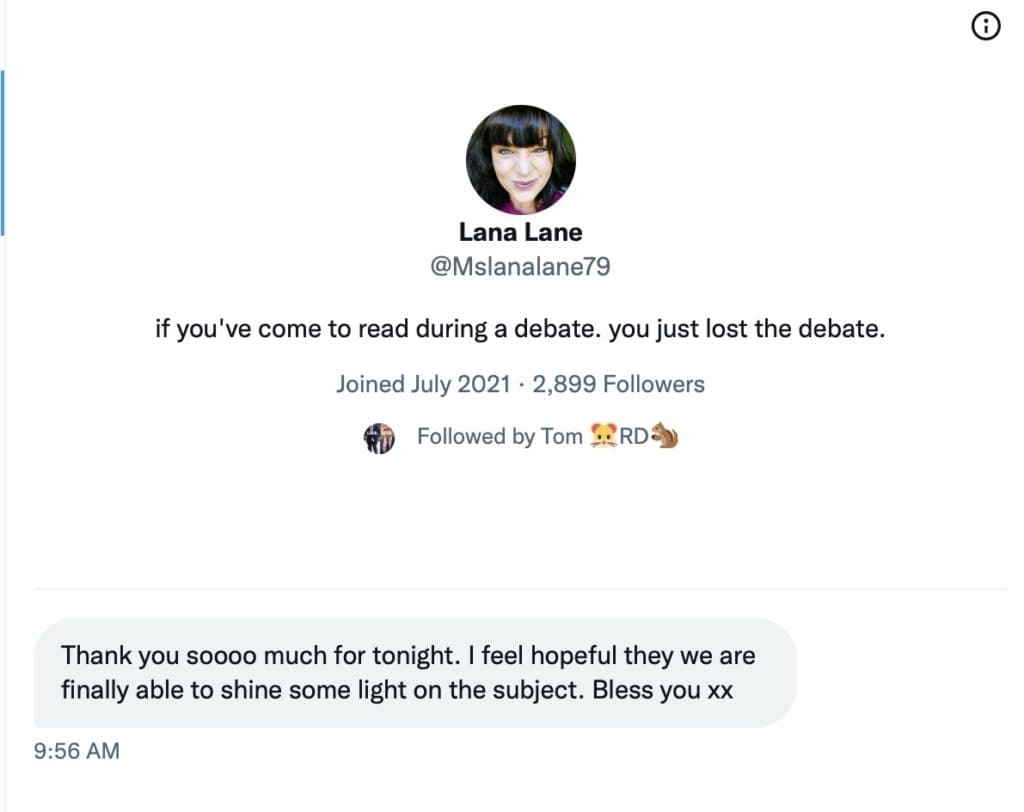
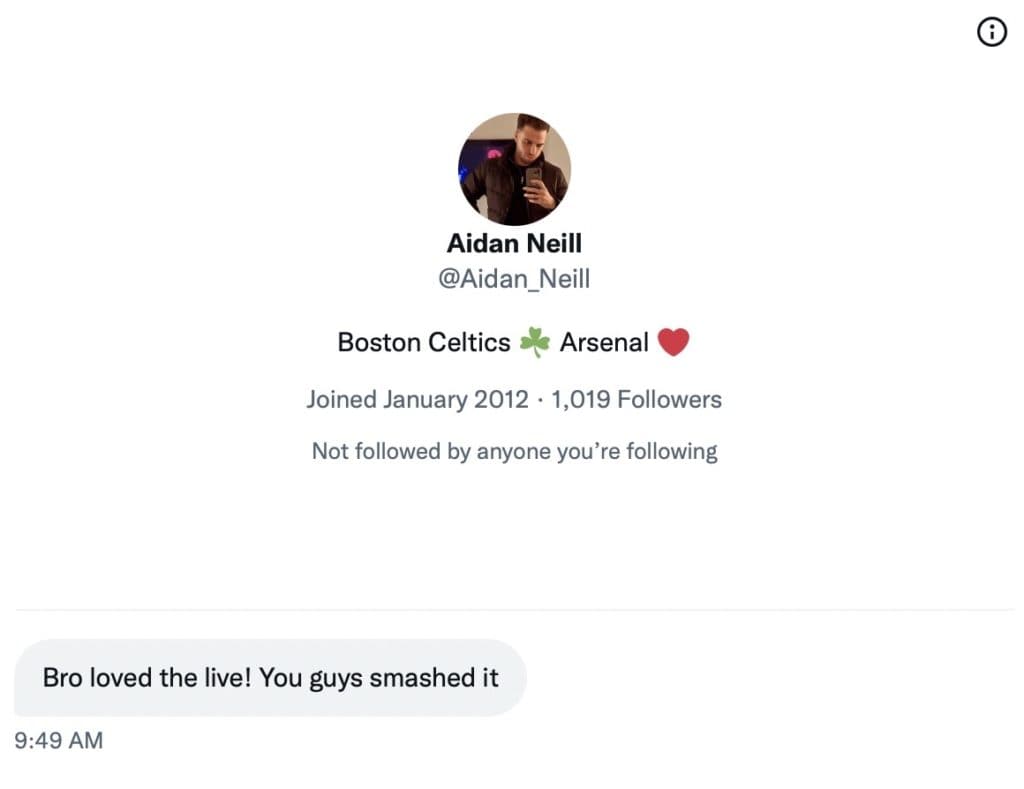
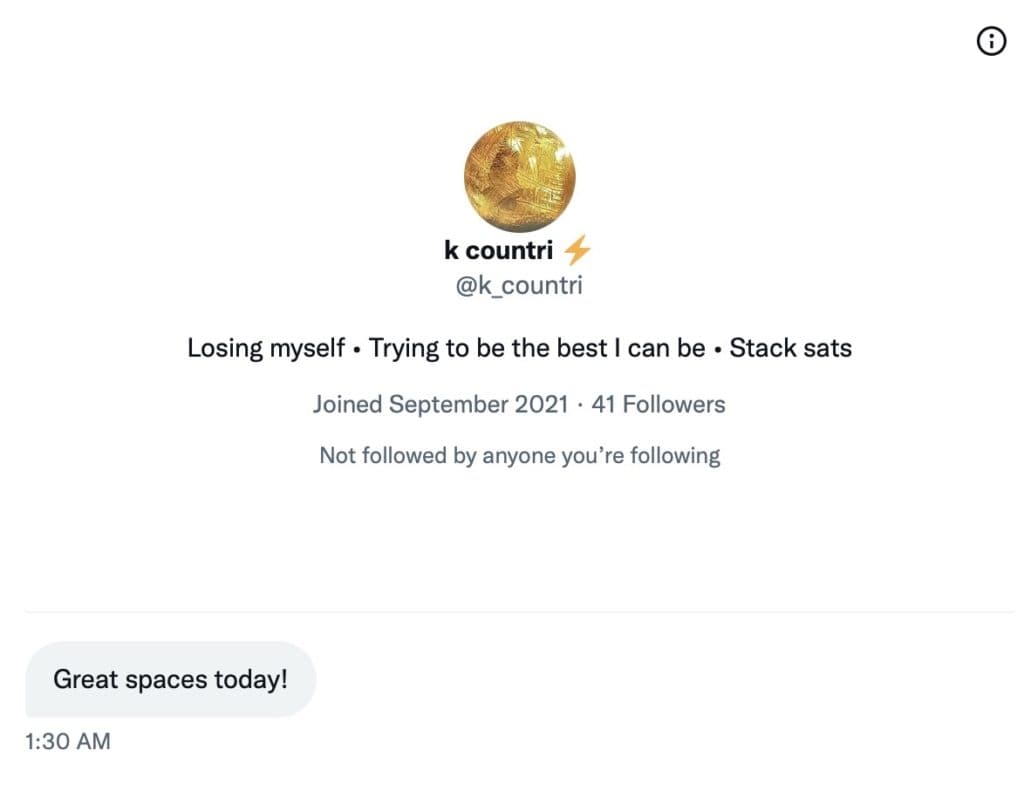
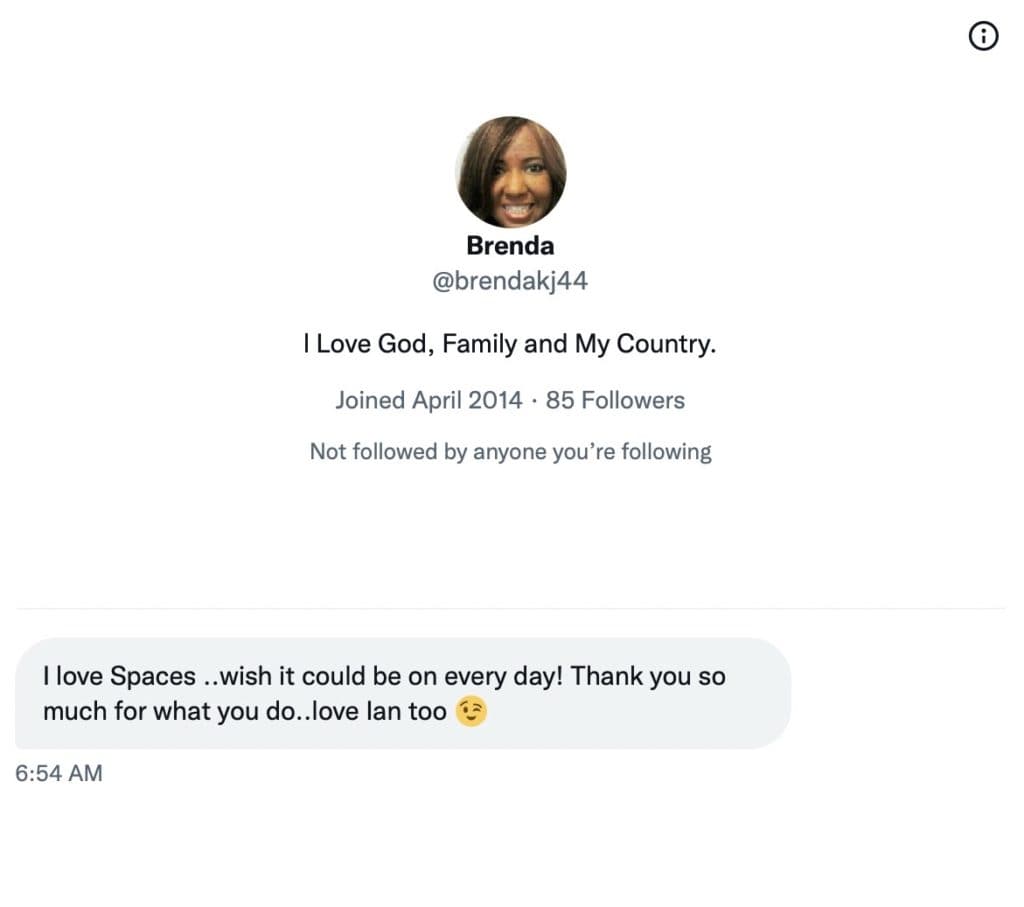
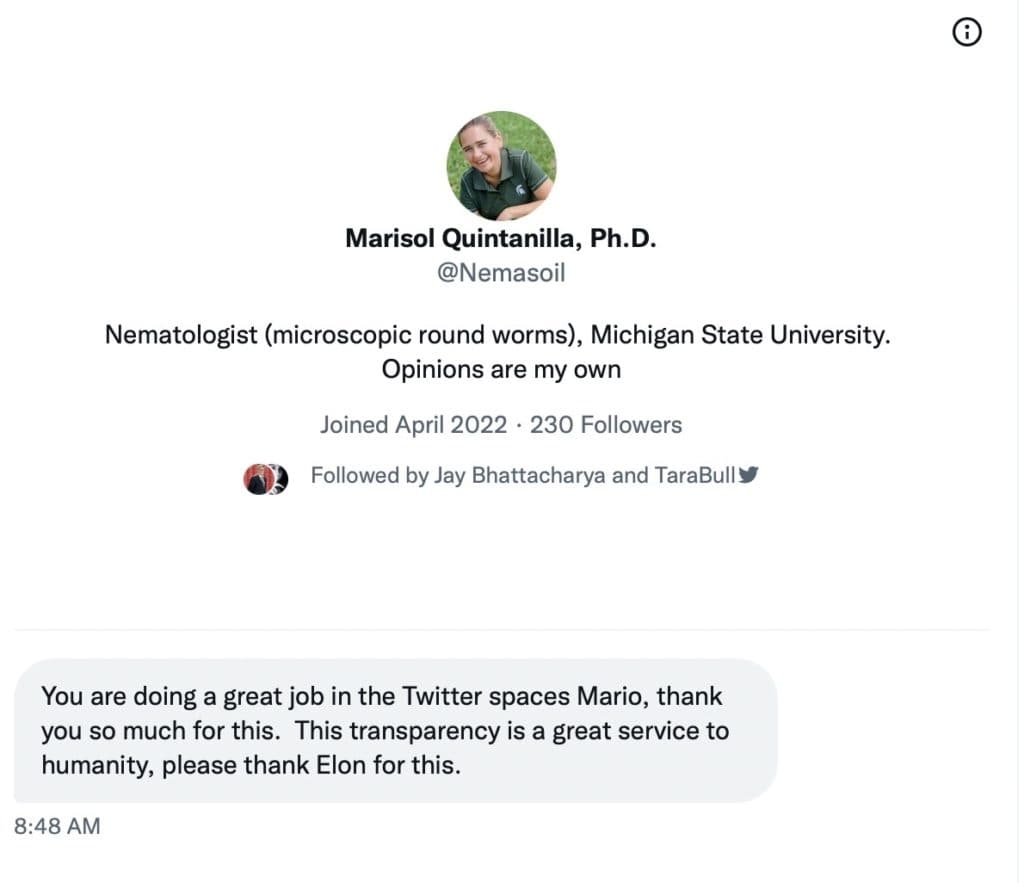
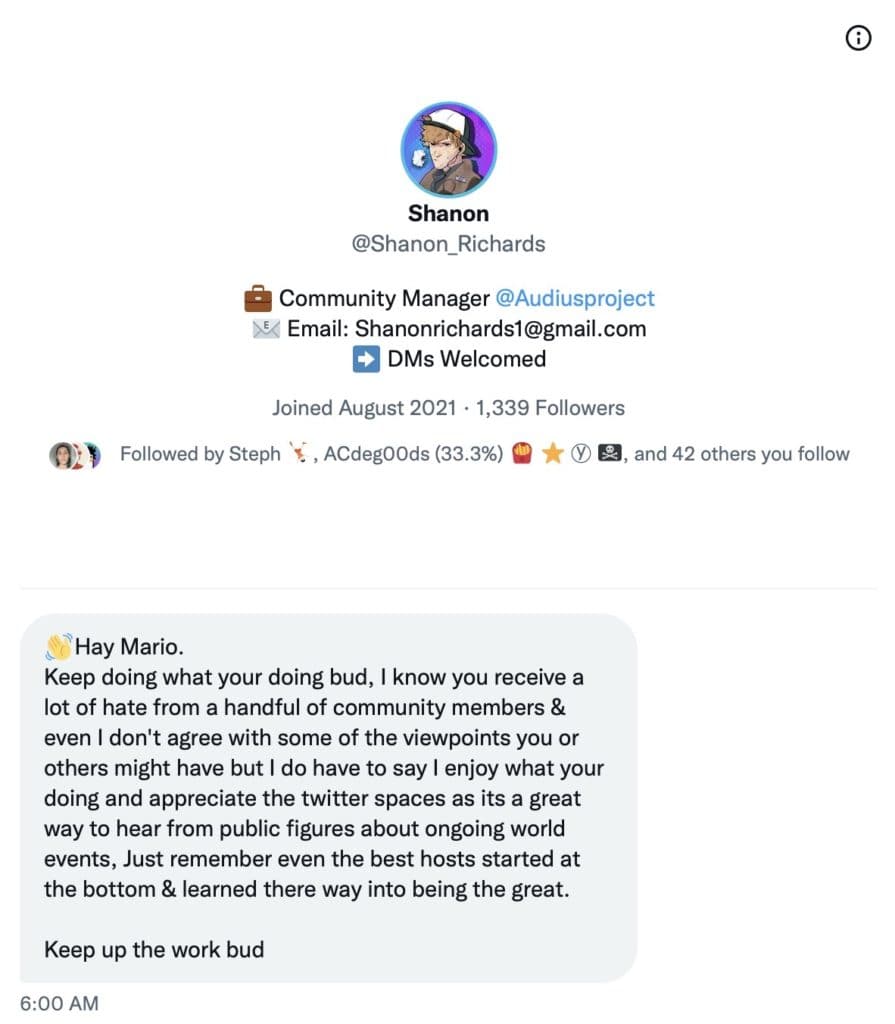
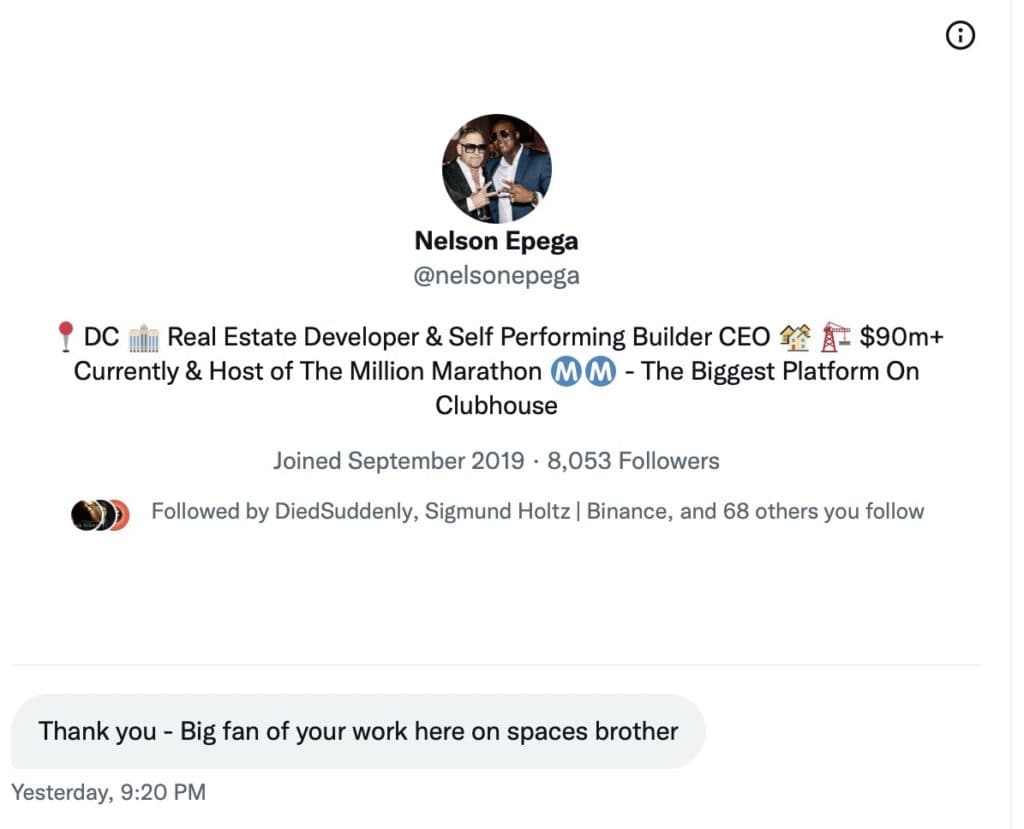
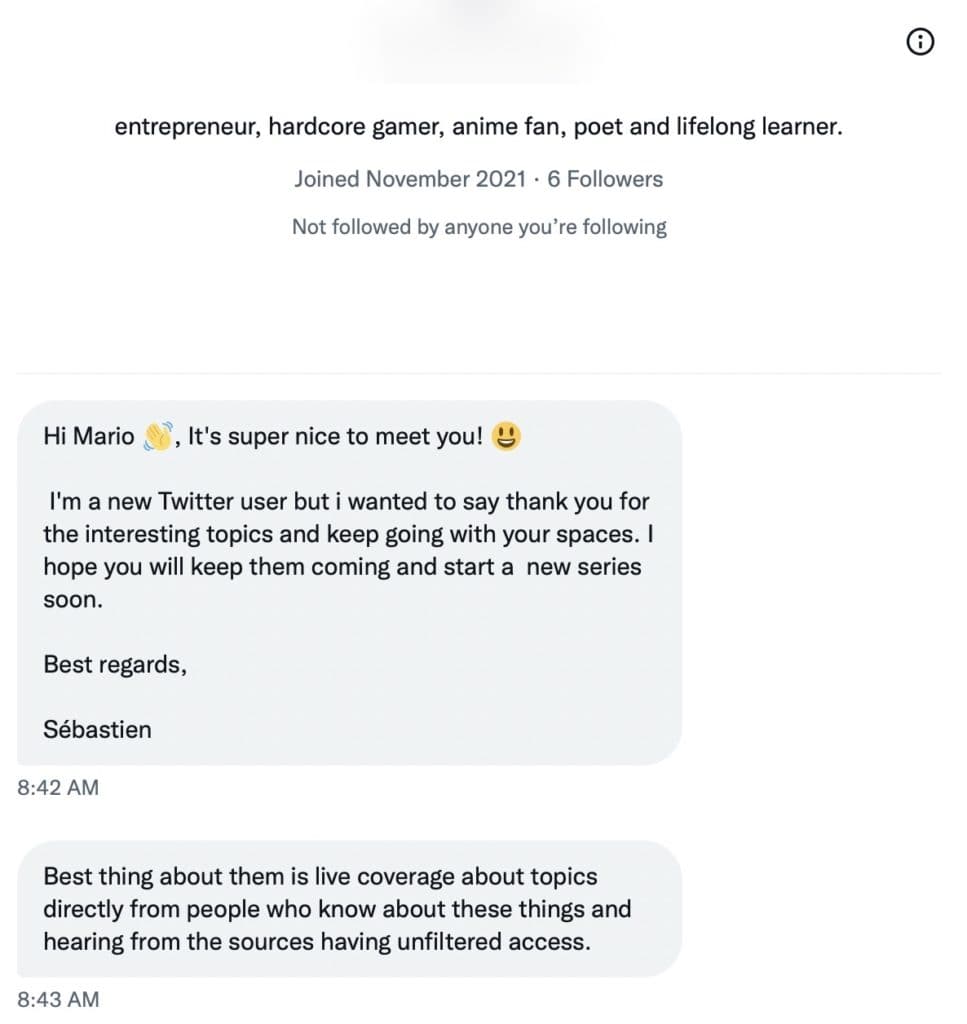
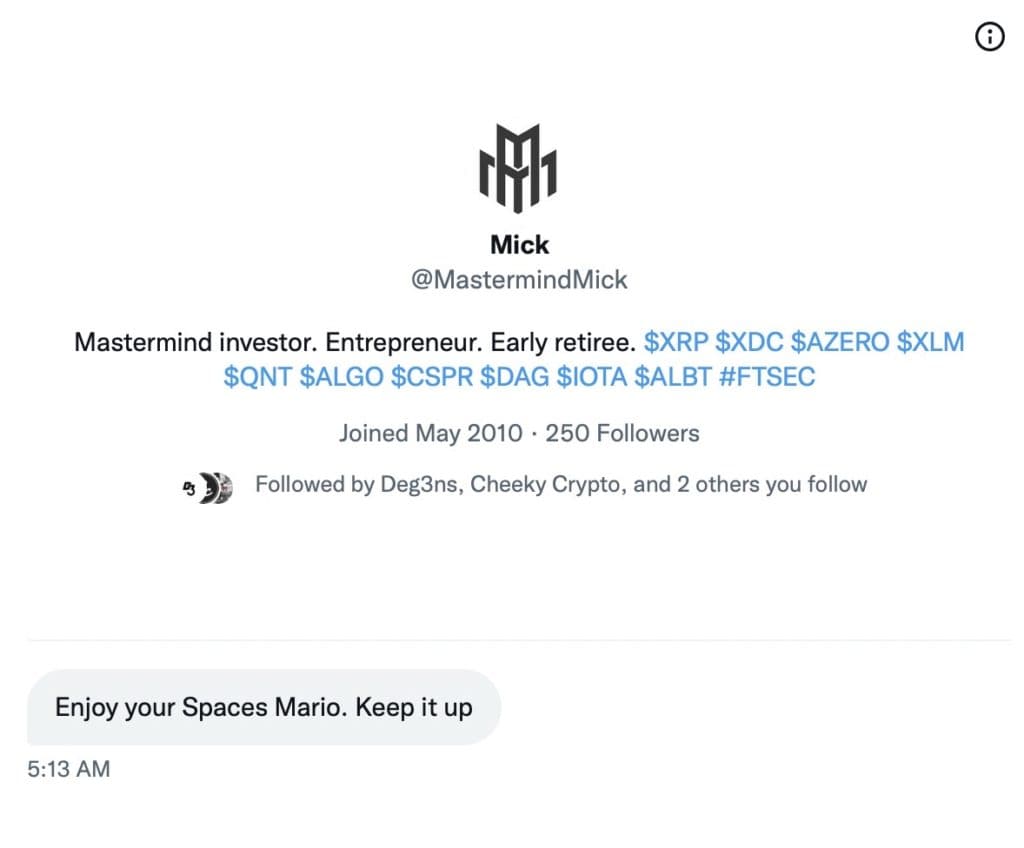
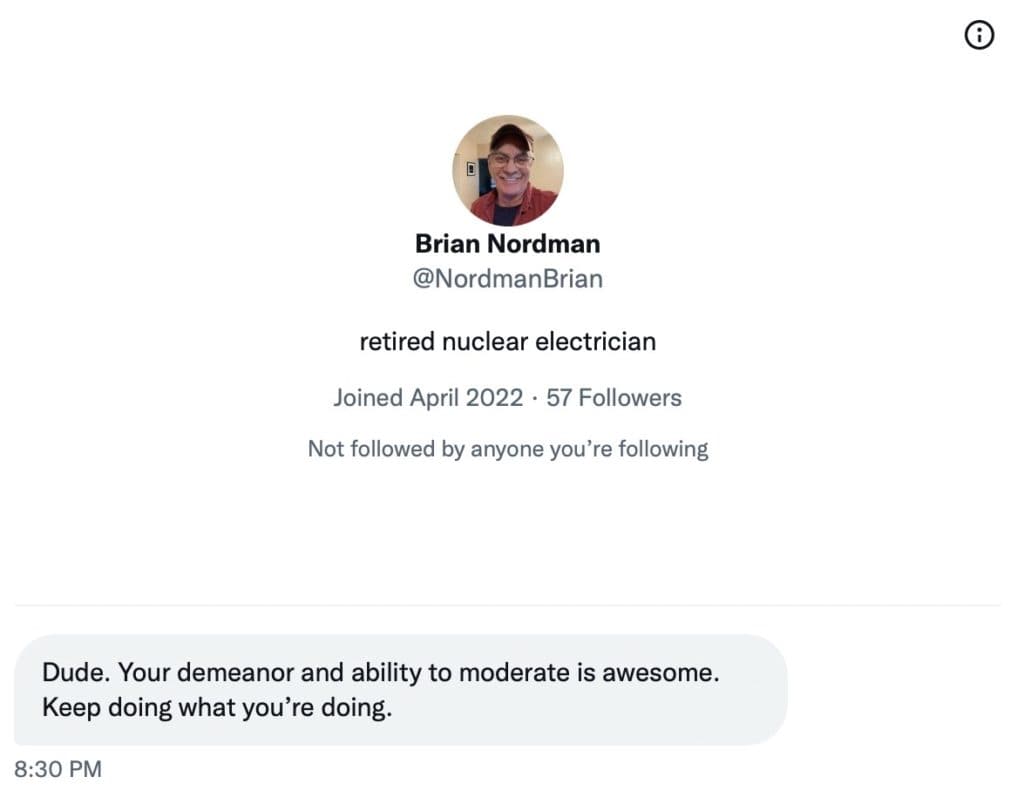
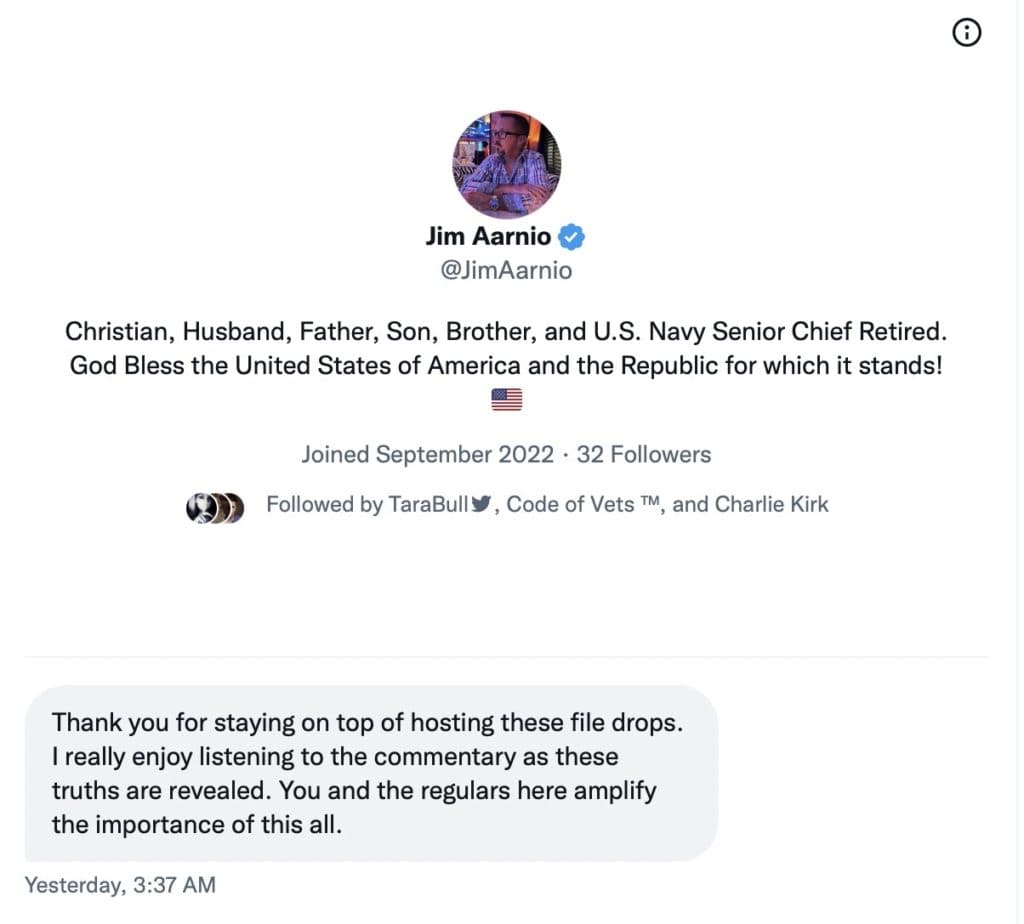
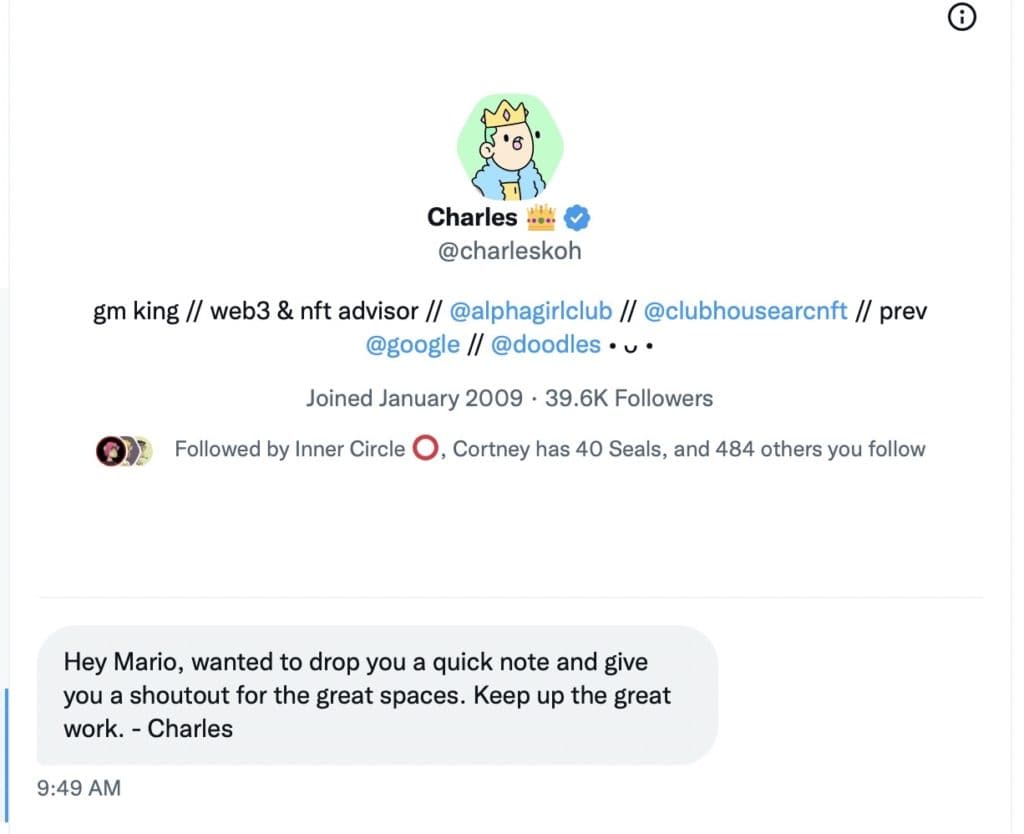
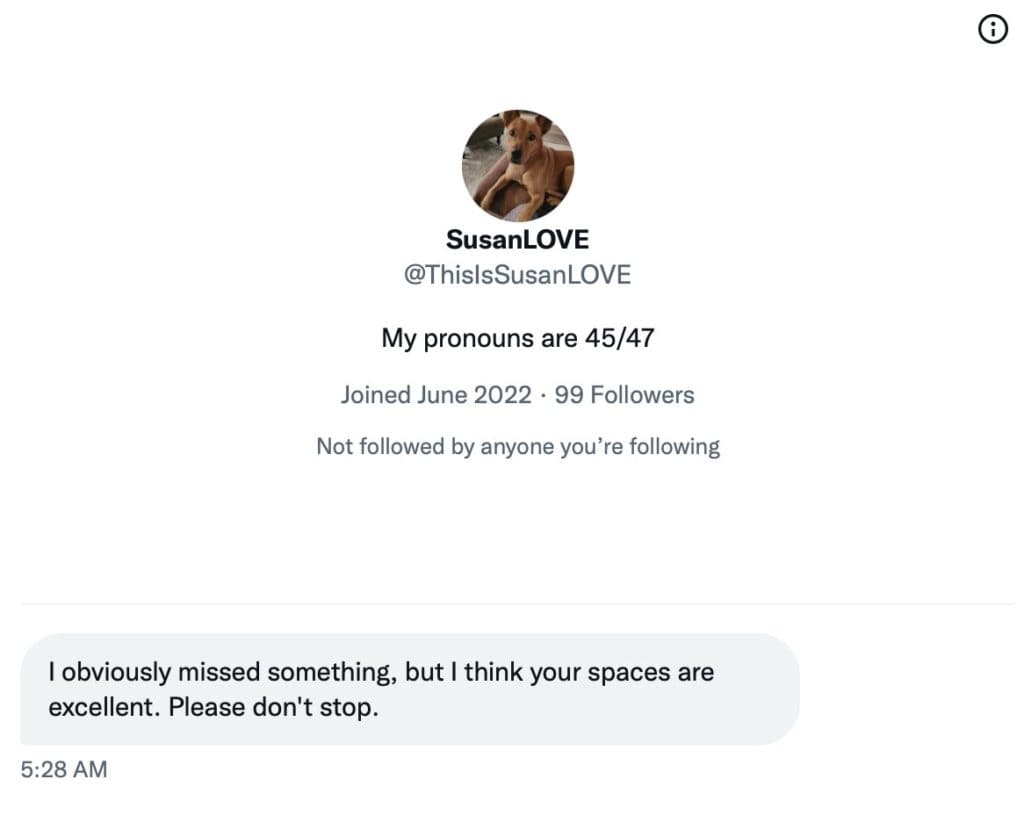
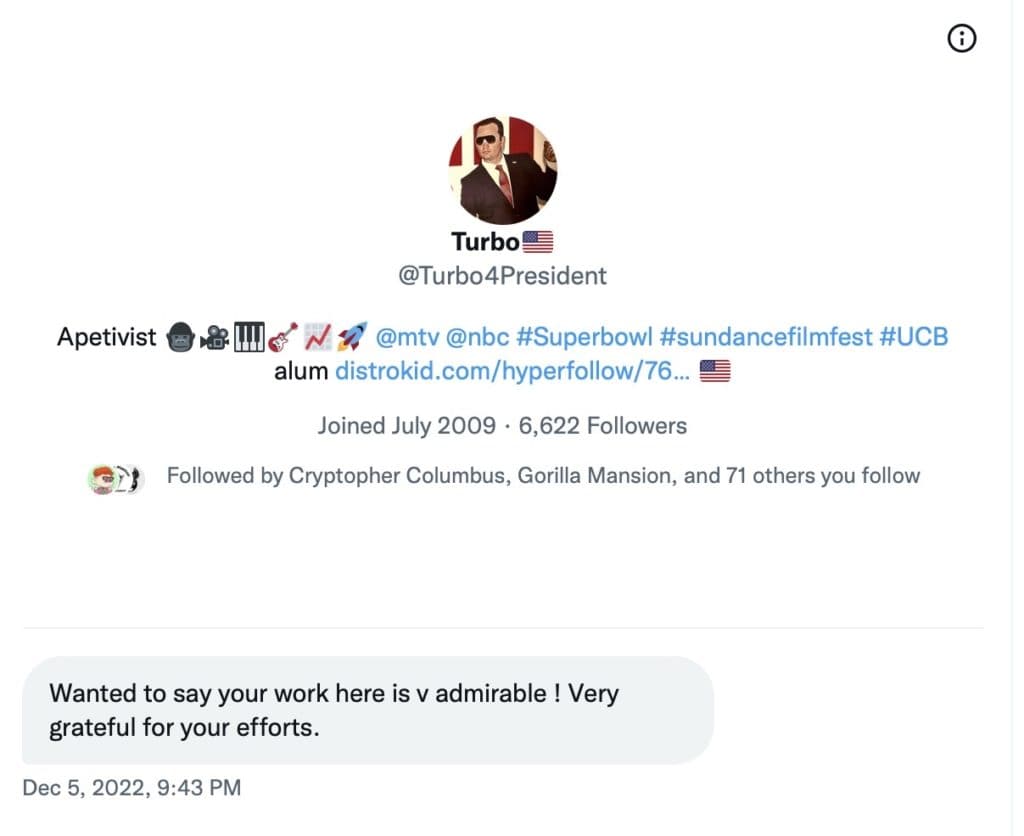
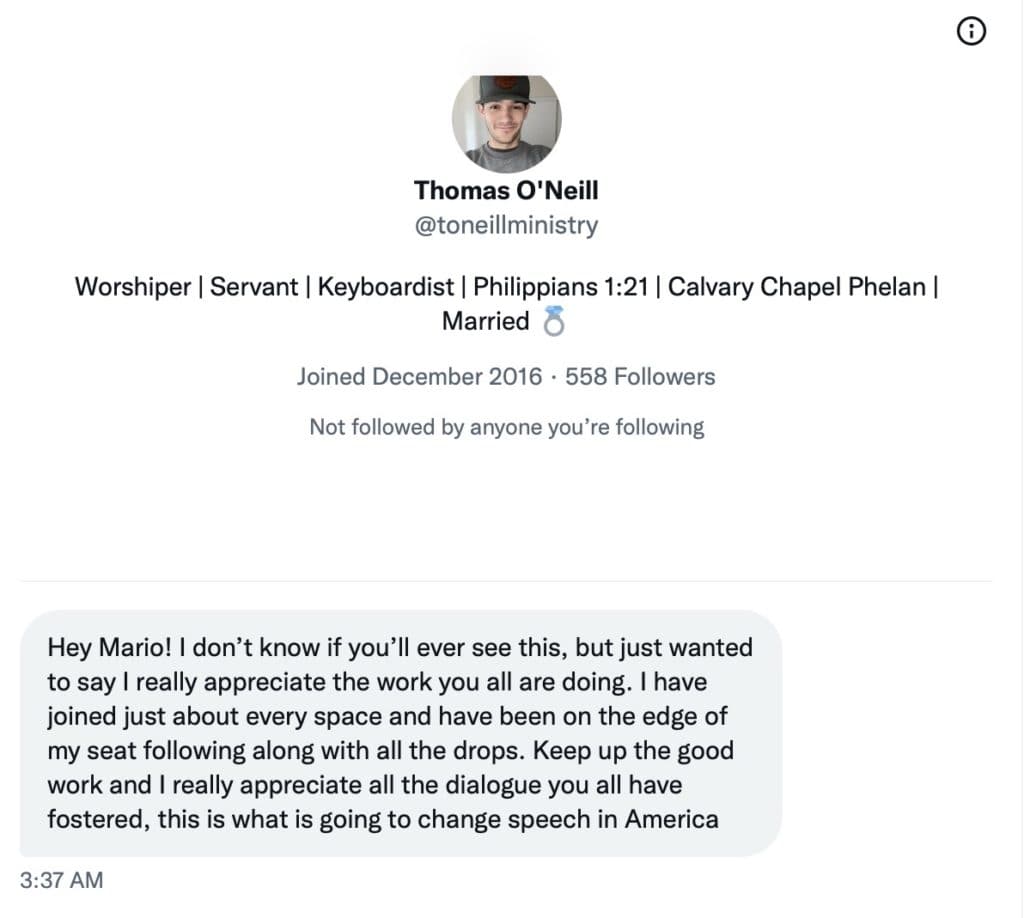
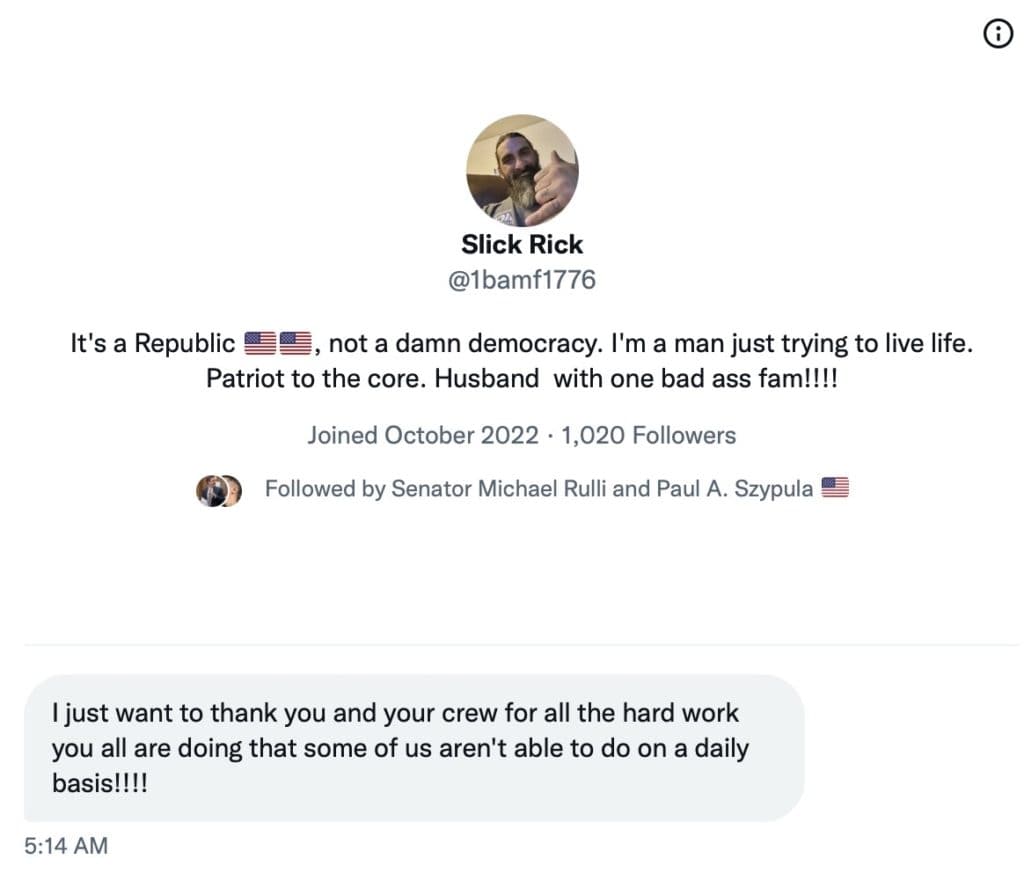
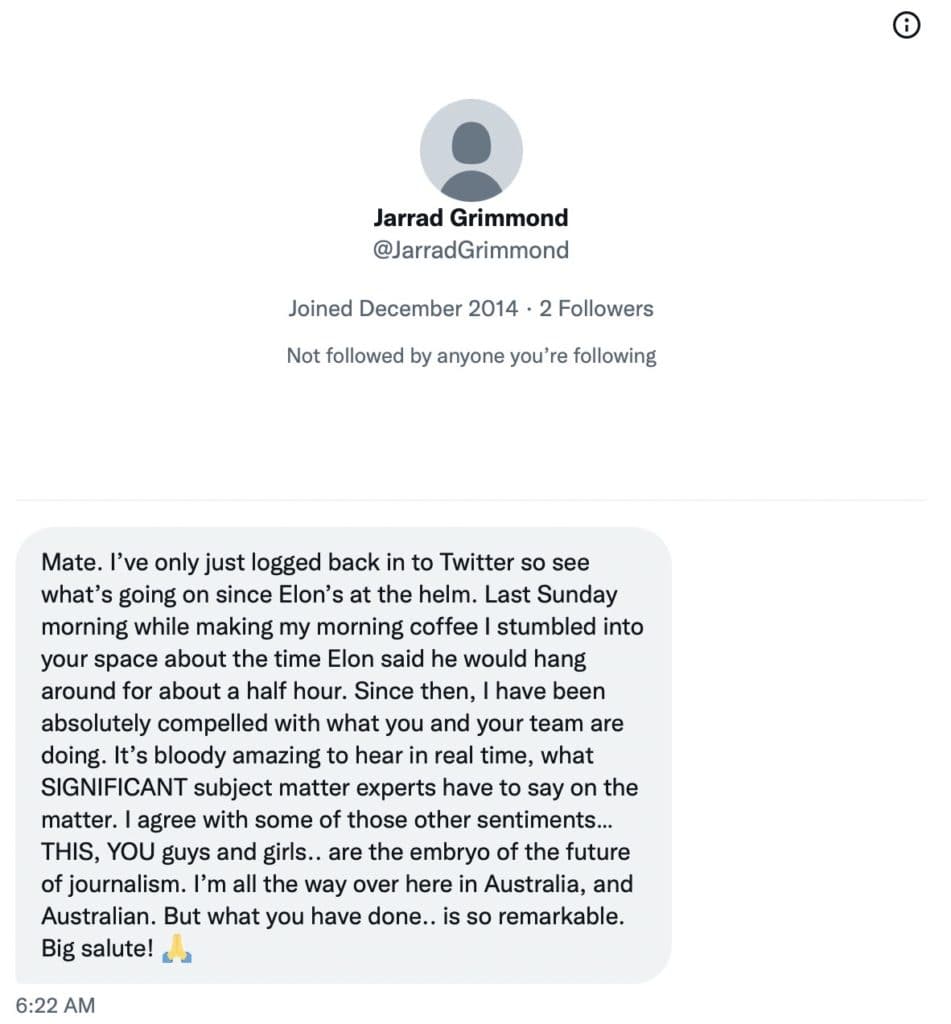
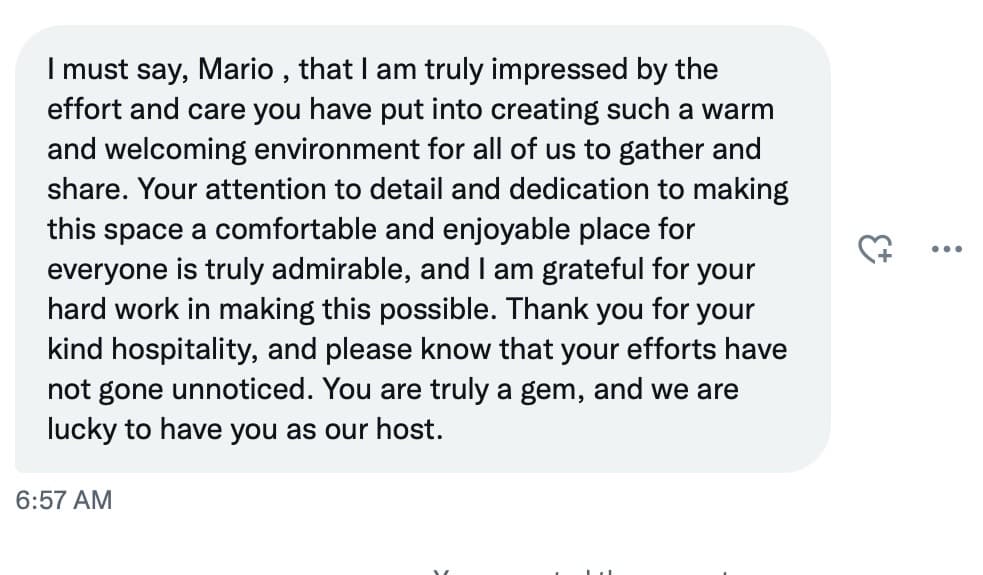
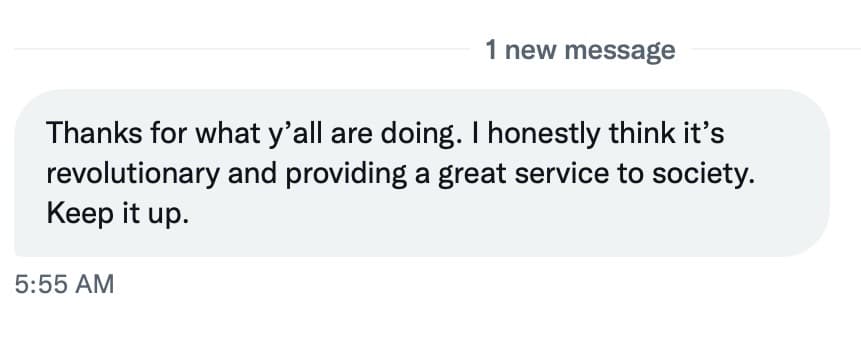
The Roundtable has become the heart of Citizen Journalism: A place where censor-free balanced debates take place daily, covering the world's most polarizing and important topics.
- Purpose: No Bias, No Echo Chambers
- Weekly Listeners: 10M+
Special Guests
Elon Musk
Special Guests
Nouriel Roubini
Special Guests
Hunter Biden
Special Guests
Rudy Giuliani
Special Guests
Marc Andreessen
Special Guests
Mick Mulvaney
Special Guests
Bill Ackman
Special Guests
Mark Cuban
Special Guests
CZ
Special Guests
Scott Adams
Special Guests
Dr Drew
Special Guests
Andrew Yang
Special Guests
Anthony Scaramucci
Special Guests
Vivek Ramaswamy
Special Guests
Michael Bay
Special Guests
Thomas Massie
Special Guests
Lauren Boebert
Special Guests
Kari Lake
Special Guests
Eric Weinstein
Special Guests
Patrick Bet David
Special Guests
Alex Jones
Special Guests
Tucker Carlson
Special Guests
Marianne Williamson
Special Guests
Andrew Tate
Special Guests
Mike Flynn
Special Guests
Mark Andreesen
Special Guests